Free AZ-500 dumps and practice testing for easy adoption of the Microsoft Azure AZ-500 certification exam

How do I pass the Microsoft Azure Security Technologies AZ-500 certification exam? Examthings shares the latest and effective Microsoft AZ-500 exam questions and answers, online practice tests, and the most authoritative Microsoft exam experts update AZ-500 exam questions throughout the year. Get the full AZ-500 exam dumps selection: https://www.leads4pass.com/az-500.html (132 Q&As). Pass the exam with ease!
Microsoft AZ-500 Exam Video
Table of Contents:
- Latest Microsoft AZ-500 google drive
- Effective Microsoft AZ-500 exam practice questions
- Latest Updated Microsoft AZ-500 Practice test 2021
- Related AZ-500 Popular Exam resources
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest Microsoft AZ-500 google drive
[PDF] Free Microsoft AZ-500 pdf dumps download from Google Drive: https://drive.google.com/open?id=1wmsYeyeykzlfx271VyQr0Fy-W8hqGt3F
Exam AZ-500: Microsoft Azure Security Technologies: https://docs.microsoft.com/en-us/learn/certifications/exams/az-500
Candidates for this exam are Microsoft Azure security engineers who implement security controls, maintain the security posture, manage identity and access, and protect data, applications, and networks. Candidates identify and remediate vulnerabilities by using a variety of security tools, implement threat protection, and respond to security incident escalations. As a Microsoft Azure security engineer, candidates often serve as part of a larger team dedicated to cloud-based management
and security and may also secure hybrid environments as part of an end-to-end infrastructure.
Candidates for this exam should have strong skills in scripting and automation; a deep understanding of networking, virtualization, and cloud N-tier architecture; and a strong familiarity with cloud capabilities, Microsoft Azure products, and services, and other Microsoft products and services.
Skills measured
The content of this exam was updated on December 4, 2019. Please download the Skills measured document below to see what changed.
- Manage identity and access (20-25%)
- Implement platform protection (35-40%)
- Manage security operations (15-20%)
- Secure data and applications (30-35%)
Latest updates Microsoft Azure Security Engineer Associate AZ-500 exam practice questions
QUESTION 1
You suspect that users are attempting to sign in to resources to which they have no access.
You need to create an Azure Log Analytics query to identify failed user sign-in attempts from the last three days. The
results must only show users who had more than five failed sign-in attempts.
How should you configure the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: 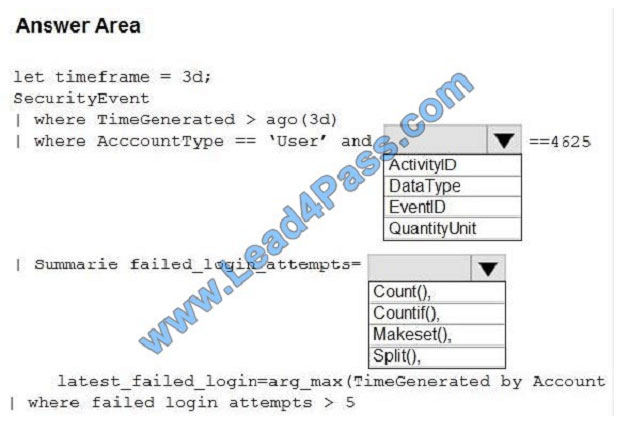
Correct Answer:
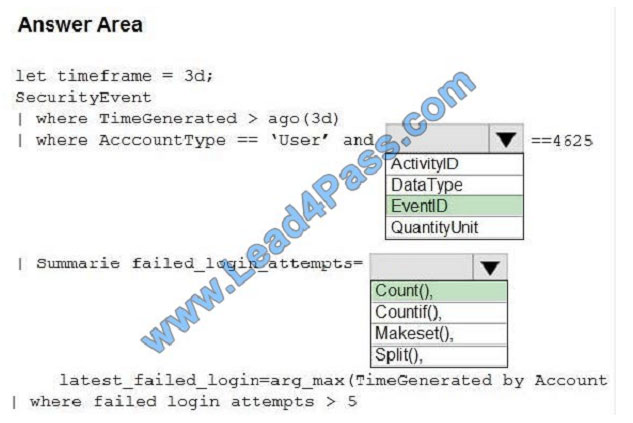
The following example identifies user accounts that failed to log in more than five times in the last day, and when they
last attempted to log in.
let timeframe = 1d; SecurityEvent | where TimeGenerated > ago(1d) | where AccountType == \\’User\\’ and EventID ==
4625 // 4625 – failed log in | summarize failed_login_attempts=count(), latest_failed_login=arg_max(TimeGenerated,
Account) by Account | where failed_login_attempts > 5 | project-away Account1
References: https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/examples
QUESTION 2
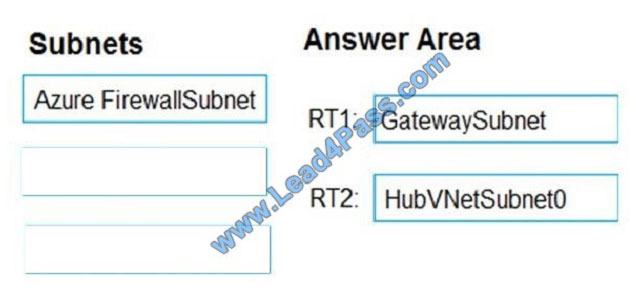
You have an Azure subscription that contains the virtual networks shown in the following table.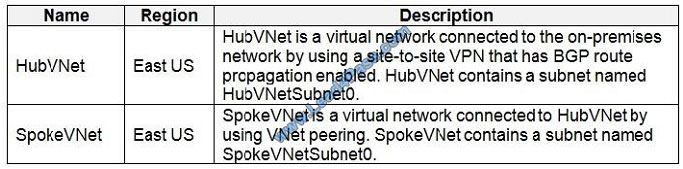
The Azure virtual machines on SpokeVNetSubnet0 can communicate with the computers on the on-premises network.
You plan to deploy an Azure firewall to HubVNet.
You create the following two routing tables:
RT1: Includes a user-defined route that points to the private IP address of the Azure firewall as a next hop address RT2:
Disables BGP route propagation and defines the private IP address of the Azure firewall as the default gateway
You need to ensure that traffic between SpokeVNetSubnet0 and the on-premises network flows through the Azure
firewall.
To which subnet should you associate each route table? To answer, drag the appropriate subnets to the correct route
tables. Each subnet may be used once, more than once, or not at all. You may need to drag the split bar between panes
or
scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
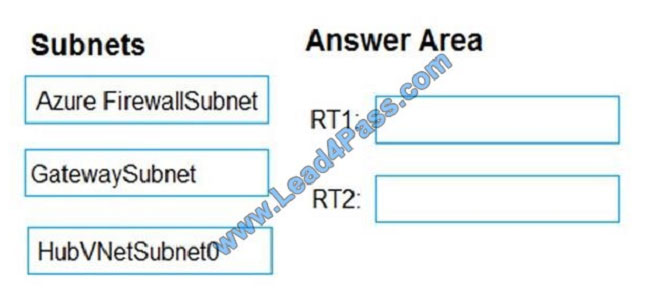
Correct Answer:
QUESTION 3
From the Azure portal, you are configuring an Azure policy.
You plan to assign policies that use the DeployIfNotExist, AuditIfNotExist, Append, and Deny effects.
Which effect requires a managed identity for the assignment?
A. AuditIfNotExist
B. Append
C. DeployIfNotExist
D. Deny
Correct Answer: C
When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity.
References: https://docs.microsoft.com/bs-latn-ba/azure/governance/policy/how-to/remediate-resources
QUESTION 4
You are evaluating the security of the network communication between the virtual machines in Sub2. For each of the
following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth
one point.
Hot Area:
Correct Answer:

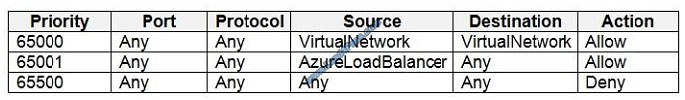
Box 1: Yes
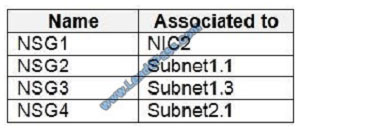
NSG1 has the inbound security rules shown in the following table.
NSG2 has the inbound security rules shown in the following table.
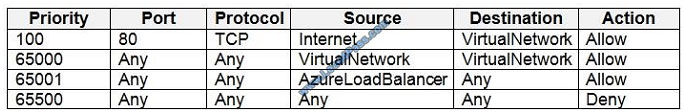
Box 2: Yes
Box 3: No
Note:
Sub2 contains the virtual machines shown in the following table.
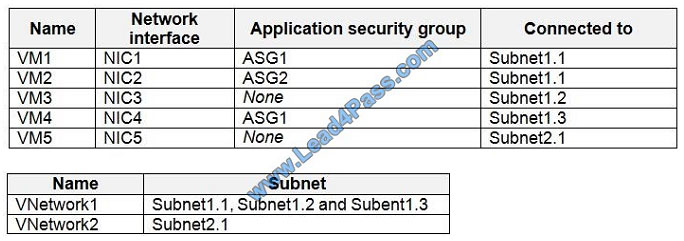
Sub2 contains the network security groups (NSGs) shown in the following table.
QUESTION 5
Your company has an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant
named contoso.com.
The company develops an application named App1. App1 is registered in Azure AD.
You need to ensure that App1 can access secrets in Azure Key Vault on behalf of the application users.
What should you configure?
A. an application permission without admin consent
B. a delegated permission without admin consent
C. a delegated permission that requires admin consent
D. an application permission that requires admin consent
Correct Answer: B
Delegated permissions – Your client application needs to access the web API as the signed-in user, but with access
limited by the selected permission. This type of permission can be granted by a user unless the permission requires
administrator consent.
Incorrect Answers:
A, D: Application permissions – Your client application needs to access the web API directly as itself (no user context).
This type of permission requires administrator consent and is also not available for public (desktop and mobile) client
applications.
References:
https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-configure-app-access-web-apis
QUESTION 6
You have an Azure subscription named Sub1.
In Azure Security Center, you have a security playbook named Play1. Play1 is configured to send an email message to
a user named User1.
You need to modify Play1 to send email messages to a distribution group named Alerts.
What should you use to modify Play1?
A. Azure DevOps
B. Azure Application Insights
C. Azure Monitor
D. Azure Logic Apps Designer
Correct Answer: D
You can change an existing playbook in Security Center to add an action, or conditions. To do that you just need to click
on the name of the playbook that you want to change, in the Playbooks tab, and Logic App Designer opens up.
References: https://docs.microsoft.com/en-us/azure/security-center/security-center-playbooks
QUESTION 7
You need to configure an access review. The review will be assigned to a new collection of reviews and reviewed by
resource owners.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions
to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
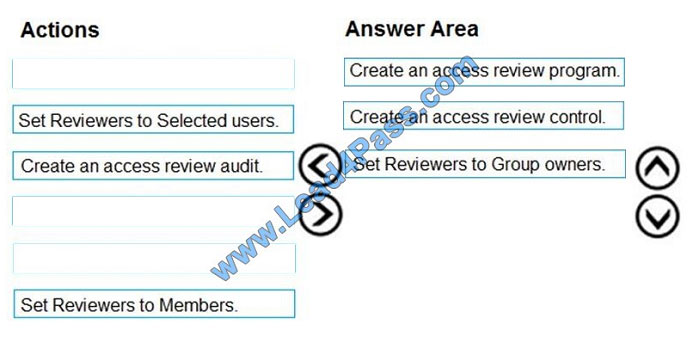
Step 1: Create an access review program Step 2: Create an access review control Step 3: Set Reviewers to Group
owners
In the Reviewers section, select either one or more people to review all the users in scope. Or you can select to have
the members review their own access. If the resource is a group, you can ask the group owners to review.

References:
https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review
https://docs.microsoft.com/en-us/azure/active-directory/governance/manage-programs-controls
QUESTION 8
You need to configure SQLDB1 to meet the data and application requirements.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from
the list of actions to the answer area and arrange them in the correct order.
Select and Place: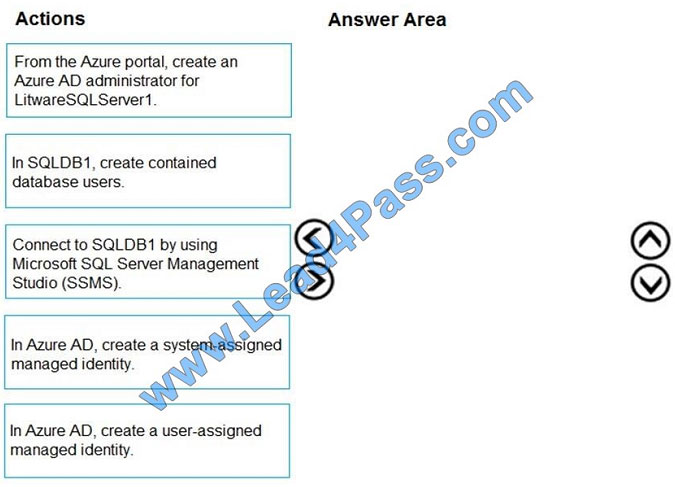
Correct Answer:
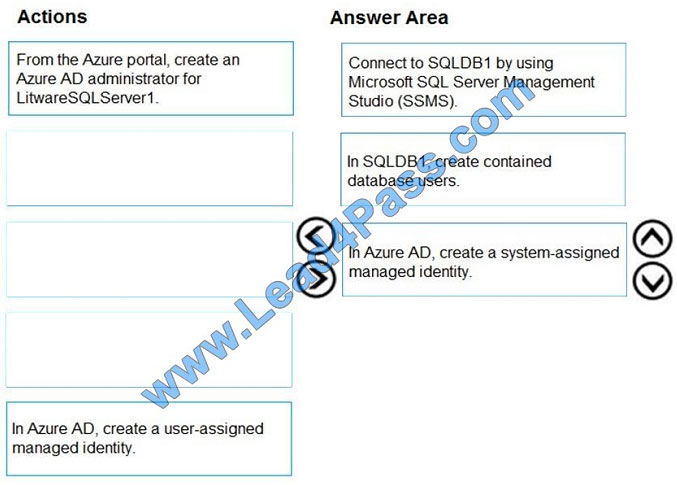
Step 1: Connect to SQLDB1 by using Microsoft SQL Server Management Studio (SSMS)
Step 2: In SQLDB1, create contained database users.
Create a contained user in the database that represents the VM\\’s system-assigned identity.
Step 3: In Azure AD,create a system-assigned managed identity.
A system-assigned identity for a Windows virtual machine (VM) can be used to access an Azure SQL server. Managed
Service Identities are automatically managed by Azure and enable you to authenticate to services that support Azure
AD
authentication, without needing to insert credentials into your code.
References:
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/tutorial-windows-vm-access-sql
QUESTION 9
You have an Azure Container Registry named Registry1.
You add role assignment for Registry1 as shown in the following table.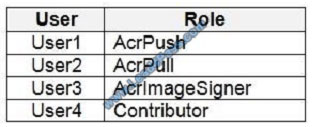
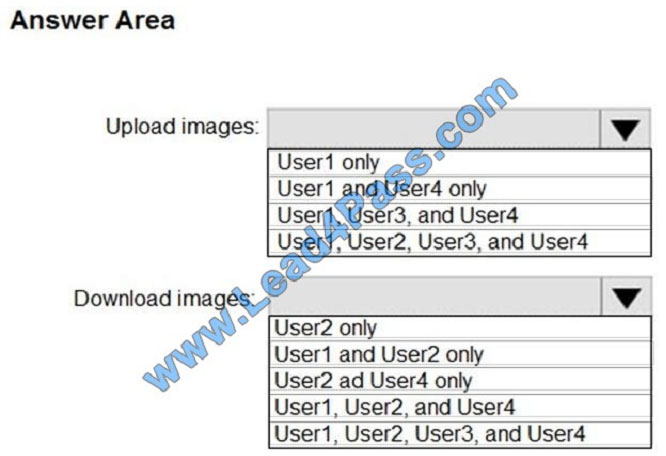
Which users can upload images to Registry1 and download images from Registry1? To answer, select the appropriate
options in the answer area. NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
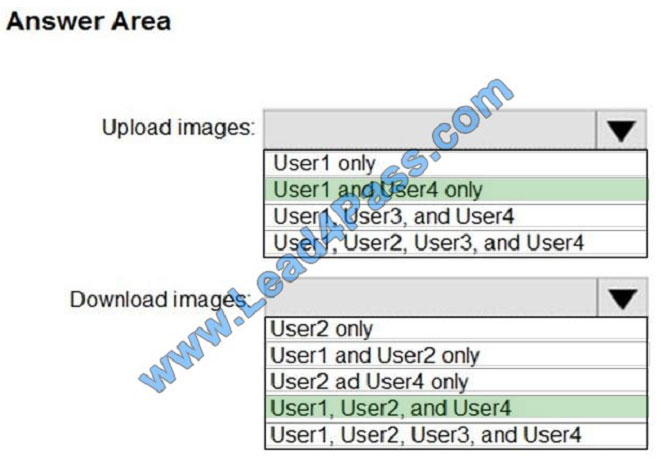
Box 1: User1 and User4 only
Owner, Contributor and AcrPush can push images.
Box 2: User1, User2, and User4
All, except AcrImagineSigner, can download/pull images.
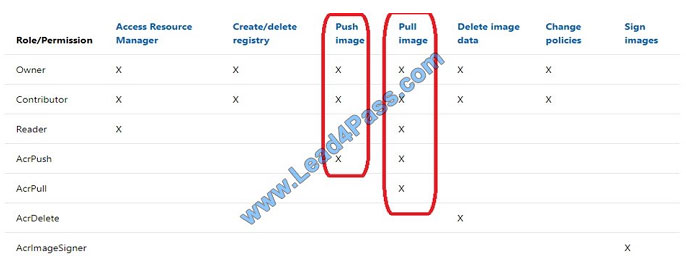
References: https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-roles
QUESTION 10
You have the Azure Information Protection conditions shown in the following table.
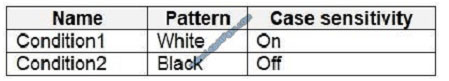
You have the Azure Information Protection labels shown in the following table.
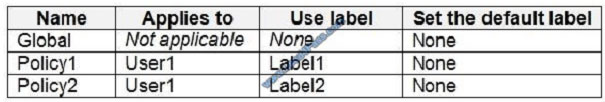
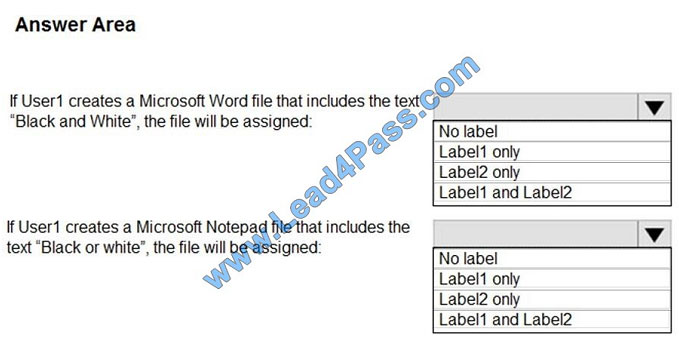
You need to identify how Azure Information Protection will label files.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
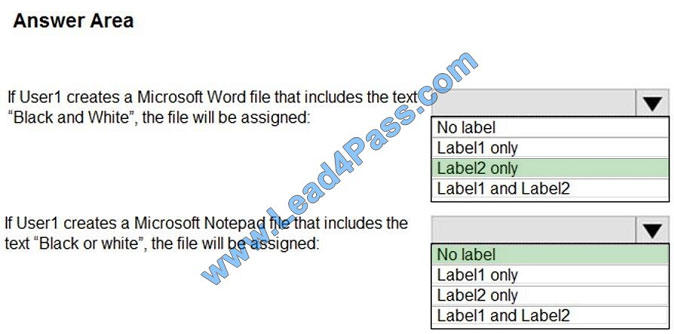
Box 1: Label 2 only How multiple conditions are evaluated when they apply to more than one label
1. The labels are ordered for evaluation, according to their position that you specify in the policy: The label positioned
first has the lowest position (least sensitive) and the label positioned last has the highest position (most sensitive).
2. The most sensitive label is applied.
3. The last sublabel is applied.
Box 2: No Label
Automatic classification applies to Word, Excel, and PowerPoint when documents are saved, and apply to Outlook when
emails are sent. Automatic classification does not apply to Microsoft Notepad.
References:
https://docs.microsoft.com/en-us/azure/information-protection/configure-policy-classification
QUESTION 11
You need to ensure that users can access VM0. The solution must meet the platform protection requirements. What
should you do?
A. Move VM0 to Subnet1.
B. On Firewall, configure a network traffic filtering rule.
C. Assign RT1 to AzureFirewallSubnet.
D. On Firewall, configure a DNAT rule.
Correct Answer: A
Explanation:
Azure Firewall has the following known issue:
Conflict with Azure Security Center (ASC) Just-in-Time (JIT) feature.
If a virtual machine is accessed using JIT, and is in a subnet with a user-defined route that points to Azure Firewall as a
default gateway, ASC JIT doesn’t work. This is a result of asymmetric routing
QUESTION 12
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear in the review screen.
You have an Azure Subscription named Sub1.
You have an Azure Storage account named Sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in Sa1 by using several shared access signatures
(SASs) and stored access policies.
You discover that unauthorized users accessed both the file service and the blob service.
You need to revoke all access to Sa1.
Solution: You create a new stored access policy.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
To revoke a stored access policy, you can either delete it, or rename it by changing the signed identifier. Changing the
signed identifier breaks the associations between any existing signatures and the stored access policy. Deleting or
renaming the stored access policy immediately effects all of the shared access signatures associated with it.
References: https://docs.microsoft.com/en-us/rest/api/storageservices/Establishing-a-Stored-Access-Policy
QUESTION 13
You need to ensure that User2 can implement PIM. What should you do first?
A. Assign User2 the Global administrator role.
B. Configure authentication methods for contoso.com.
C. Configure the identity secure score for contoso.com.
D. Enable multi-factor authentication (MFA) for User2.
Correct Answer: A
To start using PIM in your directory, you must first enable PIM.
1. Sign in to the Azure portal as a Global Administrator of your directory.
You must be a Global Administrator with an organizational account (for example, @yourdomain.com), not a Microsoft
account (for example, @outlook.com), to enable PIM for a directory.
Scenario: Technical requirements include: Enable Azure AD Privileged Identity Management (PIM) for contoso.com
References:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-getting-started
Latest Updated Microsoft AZ-500 Practice test 2021
QUESTION 1
DRAG DROP
You have an Azure Storage account named storage1 and an Azure virtual machine named VM1. VM1 has a premium
SSD-managed disk.
You need to enable Azure Disk Encryption for VM1.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions
to the answer area and arrange them in the correct order.
Select and Place:

Correct Answer:
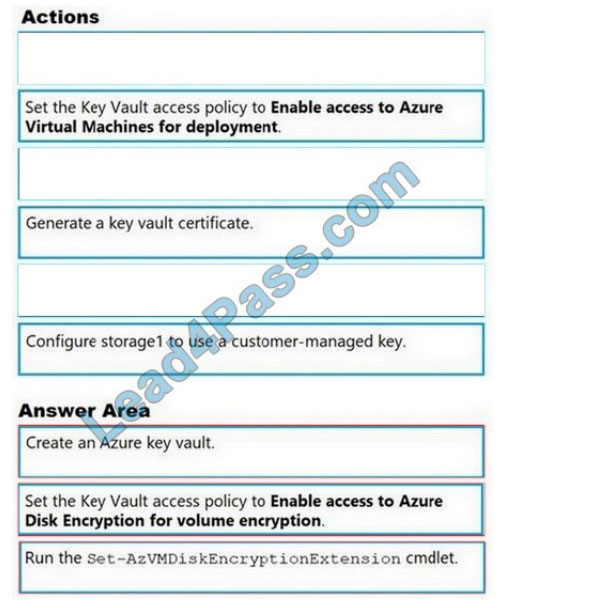
Reference: https://docs.microsoft.com/en-us/azure/virtual-machines/windows/disk-encryption-key-vault
QUESTION 2
SIMULATION
You need to configure network connectivity between a virtual network named VNET1 and a virtual network named
VNET2. The solution must ensure that virtual machines connected to VNET1 can communicate with virtual machines
connected to VNET2.
To complete this task, sign in to the Azure portal and modify the Azure resources.
A. See the below.
Correct Answer: A
You need to configure VNet Peering between the two networks. The question states, “The solution must ensure that
virtual machines connected to VNET1 can communicate with virtual machines connected to VNET2”. It doesn\\’t says the
VMs on VNET2 should be able to communicate with VMs on VNET1. Therefore, we need to configure the peering to
allow just one-way communication.
1.
In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select
VNET1. Alternatively, browse Virtual Networks in the left navigation pane.
2.
In the properties of VNET1, click on Peerings.
3.
In the Peerings blade, click Add to add a new peering.
4.
In the Name of the peering from VNET1 to a remote virtual network box, enter a name such as VNET1-VNET2 (this is the
name that the peering will be displayed as in VNET1)
5.
In the Virtual Network box, select VNET2.
6.
In the Name of the peering from the remote virtual network to the VNET1 box, enter a name such as VNET2-VNET1 (this is the
name that the peering will be displayed as in VNET2). There is an option Allow virtual network access from VNET to
the remote virtual network. This should be left as Enabled.
7.
For the option Allow virtual network access from the remote network to VNET1, click the slider button to Disabled.
8.
Click the OK button to save the changes.
Reference: https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-manage-peering
QUESTION 3
SIMULATION
You plan to use Azure Disk Encryption for several virtual machine disks.
You need to ensure that Azure Disk Encryption can retrieve secrets from the KeyVault11641655 Azure key vault.
To complete this task, sign in to the Azure portal and modify the Azure resources.
A. See the below.
Correct Answer: A
1.
In the Azure portal, type Key Vaults in the search box, select Key Vaults from the search results then select
KeyVault11641655. Alternatively, browse to Key Vaults in the left navigation pane.
2.
In the Key Vault properties, scroll down to the Settings section and select Access Policies.
3.
Select the Azure Disk Encryption for volume encryption
4.
Click Save to save the changes.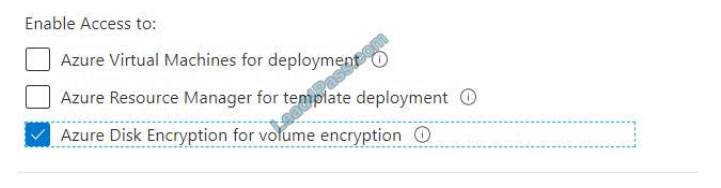
QUESTION 4
You have an Azure subscription named Subcription1 that contains an Azure Active Directory (Azure AD) tenant named
contoso.com and a resource group named RG1.
You create a custom role named Role1 for contoso.com.
You need to identify where you can use Role1 for permission delegation.
What should you identify?
A. contoso.com only
B. contoso.com and RGT only
C. contoso.com and Subscription1 only
D. contoso.com, RG1, and Subcription1
Correct Answer: D
QUESTION 5
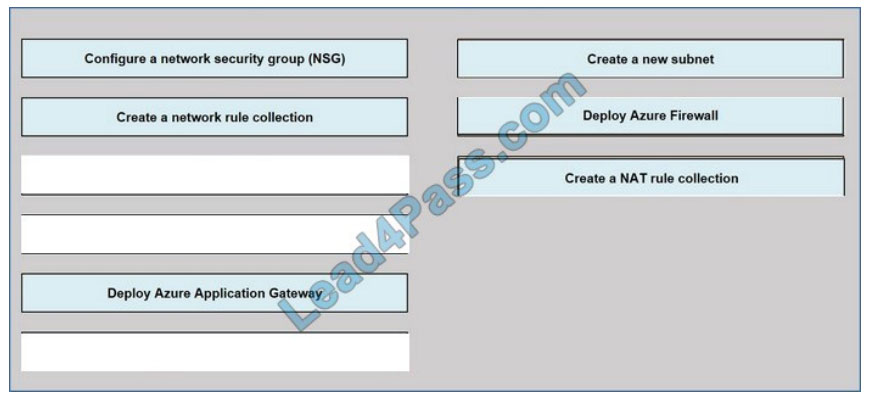
DRAG DROP
You have an Azure subscription that contains the following resources:
1.
A virtual network named VNET1 contains two subnets named Subnet1 and Subnet2.
2.
A virtual machine named VM1 has only a private IP address and connects to Subnet1.
You need to ensure that Remote Desktop connections can be established to VM1 from the internet.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions
to the answer area and arrange them in the correct order.
Select and Place: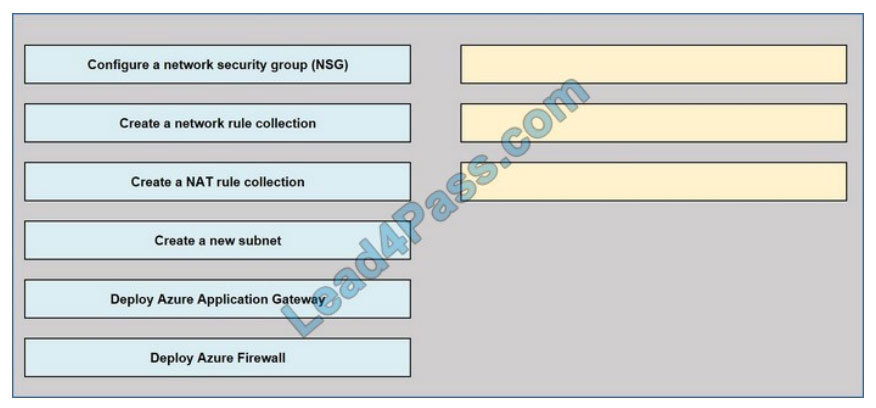
Correct Answer:
The article comes from fulldumps.com. You can get more and more complete Microsoft certification fee exam practice questions!
Related AZ-500 Popular Exam resources
| title | youtube | Microsoft | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| Microsoft Azure Security Engineer Associate | leads4pass AZ-500 dumps pdf | leads4pass AZ-500 youtube | Microsoft Azure Security Technologies | https://www.leads4pass.com/az-500.html | 132 Q&A |
leads4pass Year-round Discount Code

What are the advantages of leads4pass?
leads4pass employs the most authoritative exams from Microsoft, Cisco, CompTIA, Oracle, VMware, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader!
Choose leads4pass to pass the exam with ease!
Summarize:
It’s not easy to pass the Microsoft AZ-500 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. https://www.leads4pass.com/az-500.html provides you with the most relevant learning materials that you can use to help you prepare.