High quality CompTIA CASP CAS-002 dumps exam practice questions and answers free download from leads4pass. Latest CompTIA CASP CAS-002 dumps vce youtube demo update free shared. CompTIA CASP CAS-002 dumps exam preparation kit contains all the necessary CAS-002 questions that you need to know. “CompTIA Advanced Security Practitioner Exam” is the name of CompTIA CASP https://www.leads4pass.com/cas-002.html exam dumps which covers all the knowledge points of the real CompTIA exam. Download CompTIA CASP real CAS-002 exam questions and verified answers. 100% passing guarantee and full refund in case of failure.
Download free latest CompTIA CAS-002 dumps pdf from google drive: https://drive.google.com/open?id=0B_7qiYkH83VRVE55cV9qOGhpbG8
Download free latest CompTIA CLO-001 dumps pdf from google drive: https://drive.google.com/open?id=0B_7qiYkH83VRM1FyZGJiOUpoeVE
Vendor: CompTIA
Certifications: CASP
Exam Name: CompTIA Advanced Security Practitioner Exam
Exam Code: CAS-002
Total Questions: 532 Q&As
New CompTIA CASP CAS-002 Dumps Exam Practice Questions And Answers (1-15)
QUESTION 1
The latest independent research shows that cyber attacks involving SCADA systems grew an average of 15% per year in each of the last four years, but that this year\’s growth has slowed to around 7%. Over the same time period, the number of attacks against applications has decreased or stayed flat each year. At the start of the measure period, the incidence of PC boot loader or BIOS based attacks was negligible. Starting two years ago, the growth in the number of PC boot loader attacks has grown exponentially. Analysis of these trends would seem to suggest which of the following strategies should be employed?
A. Spending on SCADA protections should stay steady; application control spending should increase substantially and spending on PC boot loader controls should increase substantially.
B. Spending on SCADA security controls should stay steady; application control spending should decrease slightly and spending on PC boot loader protections should increase substantially.
C. Spending all controls should increase by 15% to start; spending on application controls should be suspended, and PC boot loader protection research should increase by 100%.
D. Spending on SCADA security controls should increase by 15%; application control spending should increase slightly, and spending on PC boot loader protections should remain steady.
Correct Answer: B
QUESTION 2
A startup company offering software on demand has hired a security consultant to provide expertise on data security.
The company\’s clients are concerned about data confidentiality. The security consultant must design an environment with data confidentiality as the top priority, over availability and integrity. Which of the following designs is BEST suited for this purpose?
A. All of the company servers are virtualized in a highly available environment sharing common hardware and redundant virtual storage. Clients use terminal service access to the shared environment to access the virtualized applications. A secret key kept by the startup encrypts the application virtual memory and data store.
B. All of the company servers are virtualized in a highly available environment sharing common hardware and redundant virtual storage. Clients use terminal service access to the shared environment and to access the virtualized applications. Each client has a common shared key, which encrypts the application virtual memory and data store.
C. Each client is assigned a set of virtual hosts running shared hardware. Physical storage is partitioned into LUNS and assigned to each client. MPLS technology is used to segment and encrypt each of the client\’s networks. PKI based remote desktop with hardware tokens is used by the client to connect to the application.
D. Each client is assigned a set of virtual hosts running shared hardware. Virtual storage is partitioned and assigned to each client. VLAN technology is used to segment each of the client\’s networks. PKI based remote desktop access is used by the client to connect to the application.
Correct Answer: C
QUESTION 3
A security policy states that all applications on the network must have a password length of eight characters. There are three legacy applications on the network that cannot meet this policy. One system will be upgraded in six months, and two are not expected to be upgraded or removed from the network. Which of the following processes should be followed?
A. Establish a risk matrix
B. Inherit the risk for six months
C. Provide a business justification to avoid the risk
D. Provide a business justification for a risk exception
Correct Answer: D
QUESTION 4
The security administrator is responsible for the confidentiality of all corporate data. The company\’s servers are located in a datacenter run by a different vendor. The vendor datacenter hosts servers for many different clients, all of whom have access to the datacenter. None of the racks are physically secured. Recently, the company has been the victim of several attacks involving data injection and exfiltatration. The security administrator suspects these attacks are due to several new network based attacks facilitated by having physical access to a system. Which of the following BEST describes how to adapt to the threat?
A. Apply port security to all switches, switch to SCP, and implement IPSec tunnels between devices.
B. Apply two factor authentication, require point to point VPNs, and enable log auditing on all devices.
C. Apply port security to all routers, switch to telnet, and implement point to point VPNs on all servers.
D. Apply three factor authentication, implement IPSec, and enable SNMP.
Correct Answer: A
QUESTION 5
The Chief Information Security Officer (CISO) is asking for ways to protect against zero-day exploits. The CISO is concerned that an unrecognized threat could compromise corporate data and result in regulatory fines as well as poor corporate publicity. The network is mostly flat, with split staff/guest wireless functionality. Which of the following equipment MUST be deployed to guard against unknown threats?
A. Cloud-based antivirus solution, running as local admin, with push technology for definition updates.
B. Implementation of an offsite data center hosting all company data, as well as deployment of VDI for all client computing needs.
C. Host based heuristic IPS, segregated on a management VLAN, with direct control of the perimeter firewall ACLs.
D. Behavior based IPS with a communication link to a cloud based vulnerability and threat feed.
Correct Answer: D
QUESTION 6
A company has received the contract to begin developing a new suite of software tools to replace an aging collaboration solution. The original collaboration solution has been in place for nine years, contains over a million lines of code, and took over two years to develop originally. CAS-002 dumps The SDLC has been broken up into eight primary stages, with each stage requiring an in-depth risk analysis before moving on to the next phase. Which of the following software development methods is MOST applicable?
A. Spiral model
B. Incremental model
C. Waterfall model
D. Agile model
Correct Answer: C
QUESTION 7
A developer is coding the crypto routine of an application that will be installed on a standard headless and diskless server connected to a NAS housed in the datacenter. The developer has written the following six lines of code to add entropy to the routine: 1 – If VIDEO input exists, use video data for entropy 2 – If AUDIO input exists, use audio data for entropy 3 – If MOUSE input exists, use mouse data for entropy 4 – IF KEYBOARD input exists, use keyboard data for entropy 5 – IF IDE input exists, use IDE data for entropy 6 – IF NETWORK input exists, use network data for entropy Which of the following lines of code will result in the STRONGEST seed when combined?
A. 2 and 1
B. 3 and 5
C. 5 and 2
D. 6 and 4
Correct Answer: D
QUESTION 8
The Chief Information Officer (CIO) of a technology company is likely to move away from a de-perimeterized model for employee owned devices. This is because there were too many issues with lack of patching, malware incidents, and data leakage due to lost/stolen devices which did not have full-disk encryption. The `bring your own computing\’ approach was originally introduced because different business units preferred different operating systems and application stacks. Based on the issues and user needs, which of the following is the BEST recommendation for the CIO to make?
A. The de-perimeterized model should be kept as this is major industry trend and other companies are following this direction. Advise that the issues being faced are standard business as usual concerns in a modern IT environment.
B. Update the policy to disallow non-company end-point devices on the corporate network. Develop security-focused standard operating environments (SOEs) for all required operating systems and ensure the needs of each business unit are met.
C. The de-perimeterized model should be kept but update company policies to state that non-company end-points require full disk encryption, anti-virus software, and regular patching.
D. Update the policy to disallow non-company end-point devices on the corporate network. Allow only one type of outsourced SOE to all users as this will be easier to provision, secure, and will save money on operating costs.
Correct Answer: B
QUESTION 9
The risk manager has requested a security solution that is centrally managed, can easily be updated, and protects end users\’ workstations from both known and unknown malicious attacks when connected to either the office or home network. Which of the following would BEST meet this requirement?
A. HIPS
B. UTM
C. Antivirus
D. NIPS
E. DLP
Correct Answer: A
QUESTION 10
An organization has several production critical SCADA supervisory systems that cannot follow the normal 30-day patching policy. Which of the following BEST maximizes the protection of these systems from malicious software?
A. Configure a firewall with deep packet inspection that restricts traffic to the systems
B. Configure a separate zone for the systems and restrict access to known ports
C. Configure the systems to ensure only necessary applications are able to run
D. Configure the host firewall to ensure only the necessary applications have listening ports
Correct Answer: C
QUESTION 11
A security analyst, Ann, states that she believes Internet facing file transfer servers are being attacked. Which of the following is evidence that would aid Ann in making a case to management that action needs to be taken to safeguard these servers?
A. Provide a report of all the IP addresses that are connecting to the systems and their locations
B. Establish alerts at a certain threshold to notify the analyst of high activity
C. Provide a report showing the file transfer logs of the servers
D. Compare the current activity to the baseline of normal activity
Correct Answer: D
QUESTION 12
A Chief Information Security Officer (CISO) is approached by a business unit manager who heard a report on the radio this morning about an employee at a competing firm who shipped a VPN token overseas so a fake employee could log into the corporate VPN. The CISO asks what can be done to mitigate the risk of such an incident occurring within the organization. Which of the following is the MOST cost effective way to mitigate such a risk?
A. Require hardware tokens to be replaced on a yearly basis.
B. Implement a biometric factor into the token response process.
C. Force passwords to be changed every 90 days.
D. Use PKI certificates as part of the VPN authentication process.
Correct Answer: B
QUESTION 13
Customers have recently reported incomplete purchase history and other anomalies while accessing their account history on the web server farm. Upon investigation, it has been determined that there are version mismatches of key ecommerce applications on the production web servers. The development team has direct access to the production servers and is most likely the cause of the different release versions. Which of the following process level solutions would address this problem?
A. Implement change control practices at the organization level.
B. Adjust the firewall ACL to prohibit development from directly accessing the production server farm.
C. Update the vulnerability management plan to address data discrepancy issues.
D. Change development methodology from strict waterfall to agile.
Correct Answer: A
QUESTION 14
A Chief Information Security Officer (CISO) of a major consulting firm has significantly increased the company\’s security posture; however, the company is still plagued by data breaches of misplaced assets. These data breaches as a result have led to the compromise of sensitive corporate and client data on at least 25 occasions. Each employee in the company is provided a laptop to perform company business. Which of the following actions can the CISO take to mitigate the breaches?
A. Reload all user laptops with full disk encryption software immediately.
B. Implement full disk encryption on all storage devices the firm owns.
C. Implement new continuous monitoring procedures.
D. Implement an open source system which allows data to be encrypted while processed.
Correct Answer: B
QUESTION 15
An intruder was recently discovered inside the data center, a highly sensitive area. To gain access, the intruder circumvented numerous layers of physical and electronic security measures. CAS-002 dumps Company leadership has asked for a thorough review of physical security controls to prevent this from happening again. Which of the following departments are the MOST heavily invested in rectifying the problem? (Select THREE).
A. Facilities management
B. Human resources
C. Research and development
D. Programming
E. Data center operations
F. Marketing
G. Information technology
Correct Answer: AEG
Why Select Lead 4pass?
leads4pass is the best provider of IT learning materials and the right choice for you to pass CompTIA CASP CAS-002 exam. Other brands started earlier, but the questions are not the newest the price is relatively expensive. leads4pass provide the latest real and cheapest questions and answers, help you pass CompTIA CAS-002 exam easily at first try.

Useful latest CompTIA CASP CAS-002 dumps exam practice materials and study guides in PDF format free download from leads4pass. The best and most updated latest CompTIA CASP https://www.leads4pass.com/cas-002.html dumps pdf training resources which are the best for clearing CAS-002 exam test, and to get certified by CompTIA CASP. If you are looking to get CompTIA Advanced Security Practitioner Exam certification by passing exam CAS-002 then you can pass it in one go.
Best CompTIA CASP CAS-002 dumps vce youtube demo:
https://youtu.be/UHKlO1Y4xjY
Here Are Some Reviews From Our Customers:
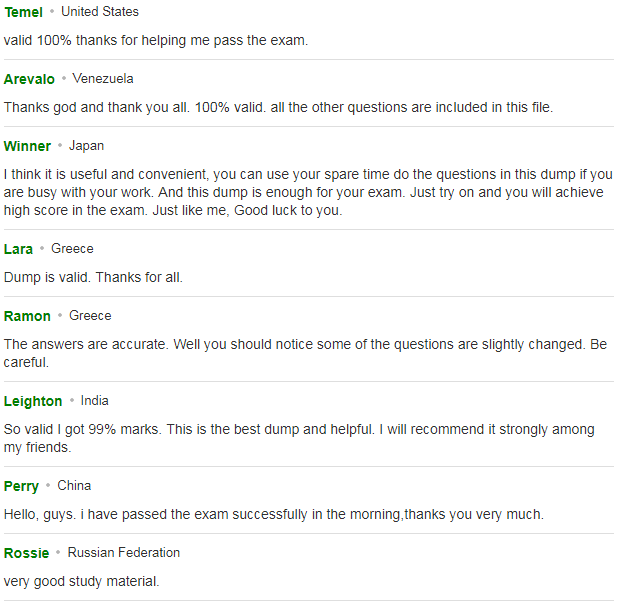
You can click here to have a review about us: https://www.resellerratings.com/store/leads4pass