
Pass the Cisco CCNA Cyber Ops 210-255 exam. “Implementing Cisco Cybersecurity Operations (SECOPS)”: https://www.leads4pass.com/210-255.html (Total Questions: 196 Q&As). I know you most want to get here for free 210-255 dumps. The latest free 210-255 exam practice questions and 210-255 pdf help you improve your skills and exam experience!
Table of Contents:
- Latest Cisco CCNA Cyber Ops 210-255 pdf
- Test your Cisco CCNA Cyber Ops 210-255 exam level
- Watch the Cisco CCNA Cyber Ops 210-255 video tutorial online
- Related 210-255 Popular Exam resources
- Get leads4pass Coupons (12% OFF)
- What are the advantages of leads4pass?
Latest Cisco CCNA Cyber Ops 210-255 pdf
[PDF] Free Cisco CCNA Cyber Ops 210-255 pdf dumps download from Google Drive: https://drive.google.com/open?id=1DvJqIWfL52ROsKHiVgNW44JumpzOCCj_
210-255 SECOPS – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/secops.html
Test your Cisco CCNA Cyber Ops 210-255 exam level
QUESTION 1
Which expression creates a filter on a host IP address or name?
A. [src|dst] host
B. [tcp|udp] [src|dst] port
C. ether [src|dst] host
D. gateway host
Correct Answer: A
QUESTION 2
Which CVSSv3 metric value increases when the attacker is able to modify all files protected by the vulnerable
component?
A. confidentiality
B. integrity
C. availability
D. complexity
Correct Answer: B
QUESTION 3
Which function does an internal CSIRT provide?
A. incident handling services across various CSIRTs
B. incident handling services for a country\\’s government
C. incident handling services for a parent organization
D. incident handling services as a service for other organization
Correct Answer: C
QUESTION 4
Which statement about threat actors is true?
A. They are any company assets that are threatened.
B. They are any assets that are threatened.
C. They are perpetrators of attacks.
D. They are victims of attacks.
Correct Answer: C
QUESTION 5
Employees are allowed access to internal websites. An employee connects to an internal website and IDS reports it as
malicious behavior. What is this example of?
A. true positive
B. false negative
C. false positive
D. true negative
Correct Answer: C
QUESTION 6
You see 100 HTTP GET and POST requests for various pages on one of your webservers. The user agent in the
requests contain php code that, if executed, creates and writes to a new php file on the webserver. Which category does
this event fall under as defined in the Diamond Model of Intrusion?
A. delivery
B. reconnaissance
C. action on objectives
D. installation
E. exploitation
Correct Answer: D
QUESTION 7
Which of the following Linux file systems not only supports journaling but also modifies important data structures of the
file system, such as the ones destined to store the file data for better performance and reliability?
A. GRUB
B. LILO
C. Ext4
D. FAT32
Correct Answer: C
QUESTION 8
Which type of analysis assigns values to scenarios to see what the outcome might be in each scenario?
A. deterministic
B. exploratory
C. probabilistic
D. descriptive
Correct Answer: A
QUESTION 9
According to NIST-SP800-61R2, which option should be contained in the issue tracking system?
A. incidents related to the current incident
B. incident unrelated to the current incident
C. actions taken by nonincident handlers
D. latest public virus signatures
Correct Answer: A
QUESTION 10
Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.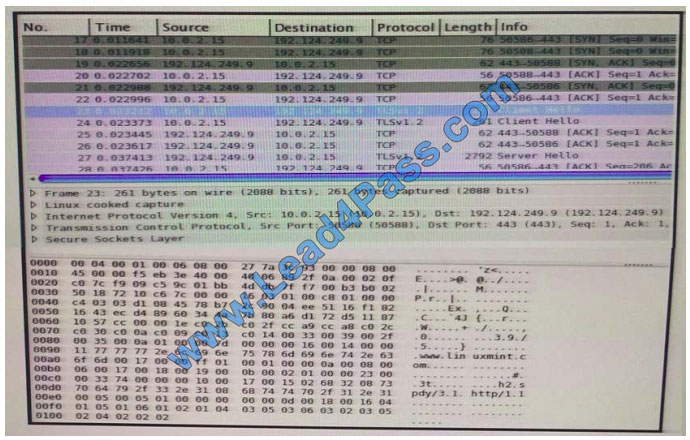
Select and Place:
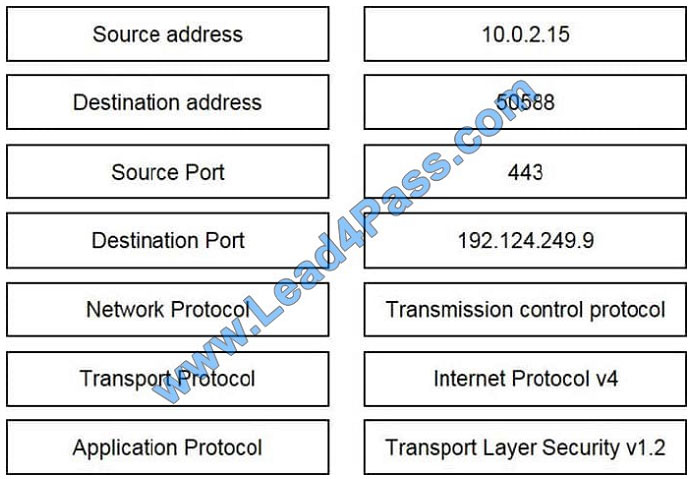
Correct Answer:
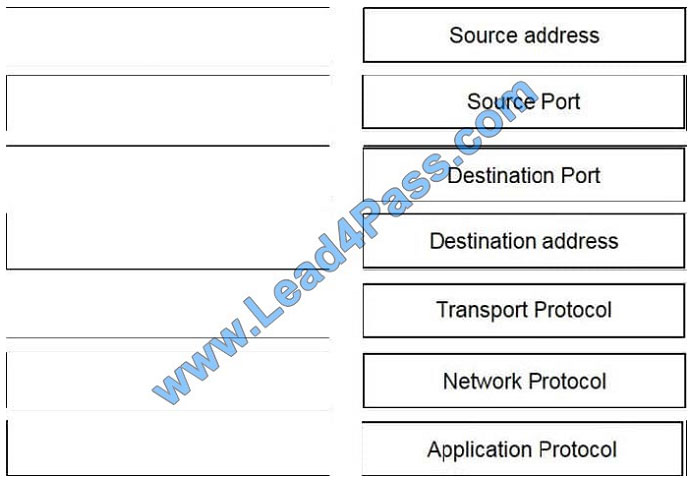
QUESTION 11
What are two security goals of data normalization? (Choose two.)
A. purge redundant data
B. reduce size of data on disk
C. increase data exposure
D. maintain data integrity
E. create data for abstraction
Correct Answer: AD
QUESTION 12
Which type verification typically consists of using tools to compute the message digest of the original and copies data,
then comparing the digests to make sure that they are the same?
A. evidence collection order
B. data integrity
C. data preservation
D. volatile data collection
Correct Answer: B
QUESTION 13
Which information must be left out of a final incident report?
A. server hardware configurations
B. exploit or vulnerability used
C. impact and/or the financial loss
D. how the incident was detected
Correct Answer: A
Watch the Cisco CCNA Cyber Ops 210-255 video tutorial online
We offer more ways to make it easier for everyone to learn, and YouTube is the best tool in the video. Follow channels: https://www.youtube.com/channel/UCXg-xz6fddo6wo1Or9eHdIQ/videos get more useful exam content.
Related 210-255 Popular Exam resources
| title | youtube | 210-255 SECOPS – Cisco | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| Cisco 210-255 | leads4pass 210-255 dumps pdf | leads4pass 210-255 youtube | 210-255 SECOPS – Cisco | https://www.leads4pass.com/210-255.html | 196 Q&A |
| Cisco CCNA Cyber Ops | https://www.leads4pass.com/210-250.html | 1132 Q&A |
Get leads4pass Coupons(12% OFF)

What are the advantages of leads4pass?
We have a number of Cisco, Microsoft, IBM, CompTIA, and other exam experts. We update exam data throughout the year.
Top exam pass rate! We have a large user base. We are an industry leader! Choose leads4pass to pass the exam with ease!

Summarize:
Free Cisco Proctored Exams for Validating Knowledge 210-255 exam exercise questions and answers, 210-255 pdf and 210-255 video practice questions. These will help you improve your exam experience.
I know you want to easily get 210-255 certification! It’s not hard! Experts recommend https://www.leads4pass.com/210-255.html help you easily get certified.