There will be more people taking the exam in October. What is the real pass rate?
The latest update of the Microsoft MD-100 exam dumps comes from leads4pass to help you pass the exam 100%.
Here you can get free Microsoft MD-100 exam practice questions online practice test. To get the complete Microsoft MD-100 exam dumps, please visit https://www.leads4pass.com/md-100.html (PDF +VCE). You can choose PDF or VCE. Both modes can help you succeed Pass the exam.
Free Microsoft MD-100 exam PDF in Google Drive
Share free Microsoft MD-100 exam PDF from a part of leads4pass MD-100 exam dumps:
https://drive.google.com/file/d/1cB-EJPZiqQB3Lxr4PXNVjkDyK6_4NSXU/
[Update Oct 2022] Microsoft MD-100 PDF: https://drive.google.com/file/d/1F_eR7y_SRoRqlecYvmcefuTjHGIeLboE/
Latest Updated Microsoft MD-100 Online Practice Test
| Number of exam questions | Exam name | From | Release time | Previous issue |
| 13 | Windows Client (MD-100) | leads4pass | Sep 24, 2022 | Apr 28, 2022 |
The latest Microsoft MD-100 exam practice questions are from the dumps part of leads4pass MD-100,
and the answers to the questions will be announced at the end of the article
QUESTION 1:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear on the review screen.
You have a computer that runs Windows 10. The computer contains a folder. The folder contains sensitive data.
You need to log which user reads the contents of the folder and modifies and deletes files in the folder.
Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in the local
Group Policy, you configure Audit system events.
Does this meet the goal?
A. Yes
B. No
Files and folders are objects and are audited through object access, not though system events.
References: https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html
QUESTION 2:
You need to meet the technical requirement for User6. What should you do?
A. Add User6 to the Remote Desktop Users group in the domain.
B. Remove User6 from Group2 in the domain.
C. Add User6 to the Remote Desktop Users group on Computer2.
D. And User6 to the Administrators group on Computer2.
QUESTION 3:
A user named User1 has a computer named Computer1 that runs Windows 10.
User1 connects to a Microsoft Azure virtual machine named VM1 by using Remote Desktop. User1 creates a VPN connection named VPN1 to connect to a partner organization.
When the VPN1 connection is established, User1 cannot connect to VM1. When User1 disconnects from VPN1, the user can connect to VM1.
You need to ensure that User1 can connect to VM1 while connected to VPN1.
What should you do?
A. From the proxy settings, add the IP address of VM1 to the bypass list to bypass the proxy.
B. From the properties of VPN1, clear the Use default gateway on the remote network check box.
C. From the properties of the Remote Desktop connection to VM1, specify a Remote Desktop Gateway (RD Gateway).
D. From the properties of VPN1, configure a static default gateway address.
References: https://www.stevejenkins.com/blog/2010/01/using-the-local-default-gateway-with-a-windows-vpnconnection/
QUESTION 4:
You have a Microsoft Azure Active Directory (Azure AD) tenant.
Some users sign in to their computers by using Windows Hello for Business.
A user named User1 purchases a new computer and joins the computer to Azure AD.
User1 is not able to use Windows Hello for Business on his computer. User1 sign-in options are shown on the exhibit
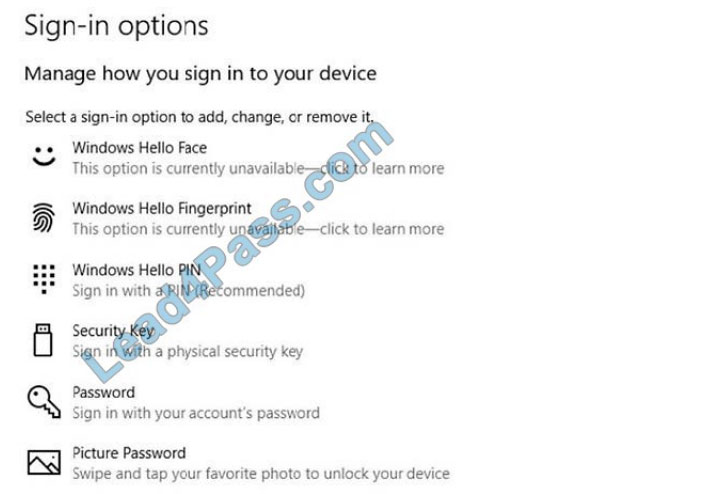
You open Device Manager and confirm that all the hardware works correctly.
You need to ensure that User1 can use Windows Hello for Business facial recognition to sign in to the computer. What should you do first?
A. Purchase an infrared (IR) camera.
B. Upgrade the computer to Windows 10 Enterprise.
C. Enable UEFI Secure Boot.
D. Install a virtual TPM driver.
Windows Hello facial recognition requires an infrared (IR) camera. If your device does not have an infrared camera (or any other biometric device such as a fingerprint scanner), you will see the message shown in the exhibit. The question states that Device Manager shows all hardware is working properly. Therefore, it is not the case that the computer has an IR camera but it isn\\’t working properly. The problem must be that the computer does not have an IR camera.
Incorrect Answers:
B: Windows 10 Enterprise is not required for Windows Hello. Windows Hello also works on Windows 10 Pro.
C: UEFI Secure Boot is not required for Windows Hello.
D: A virtual TPM driver is not required for Windows Hello.
References: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-planningguide
QUESTION 5:
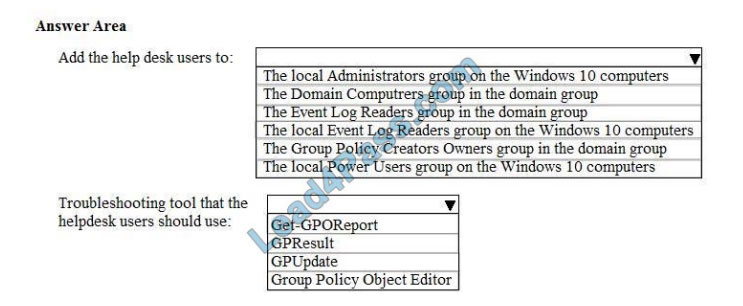
You need to meet the technical requirements of the helpdesk users.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
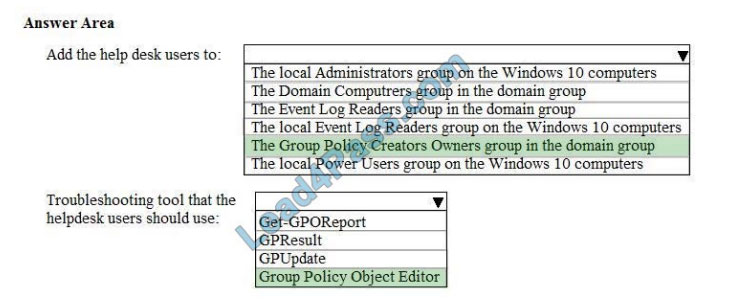
References: https://www.itprotoday.com/compute-engines/what-group-policy-creator-owners-group
QUESTION 6:
You have a computer that runs Windows 10 and is joined to Azure Active Directory (Azure AD). You attempt to open Control Panel and receive the error message shown on the following exhibit.
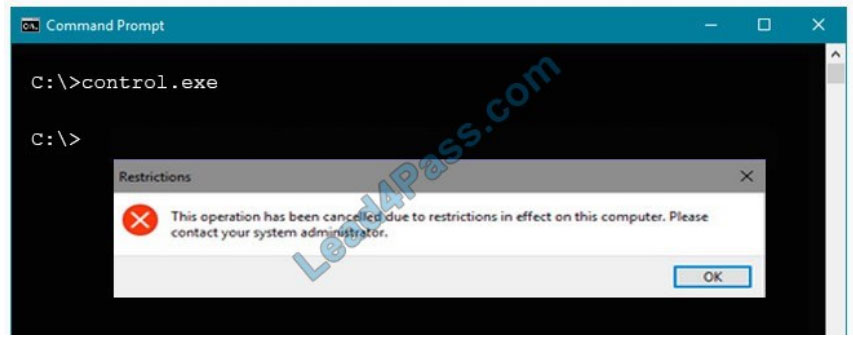
You need to be able to access Control Panel.
What should you modify?
A. the PowerShell execution policy
B. the local Group Policy
C. the Settings app
D. a Group Policy preference
References: https://windows10skill.com/this-operation-has-been-cancelled-due-to-restrictions-in-effect-on-this-pc/
QUESTION 7:
Your network contains an Active Directory domain that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. Your company purchases a Microsoft 365 subscription.
You need to migrate the Documents folder of users to Microsoft OneDrive for Business.
What should you configure?
A. One Drive Group Policy settings
B. roaming user profiles
C. Enterprise State Roaming
D. Folder Redirection Group Policy settings
You need to configure a Group Policy Object (GPO) with the OneDrive settings required to redirect the Documents folder of each user to Microsoft 365.
Importing the OneDrive group policy template files into Group Policy adds OneDrive-related settings that you can configure in your Group Policy.
One of the group policy settings enables you to redirect “Known Folders” to OneDrive for business. Known folders are Desktop, Documents, Pictures, Screenshots, and Camera Roll.
There are two primary advantages of moving or redirecting Windows-known folders to OneDrive for the users in your domain:
1. Your users can continue using the folders they\\’re familiar with. They don’t have to change their daily work habits to save files to OneDrive.
2. Saving files to OneDrive backs up your user’s \\’ data in the cloud and gives them access to their files from any device.
QUESTION 8:
You have computers that run Windows 10 and are configured as shown in the following table.
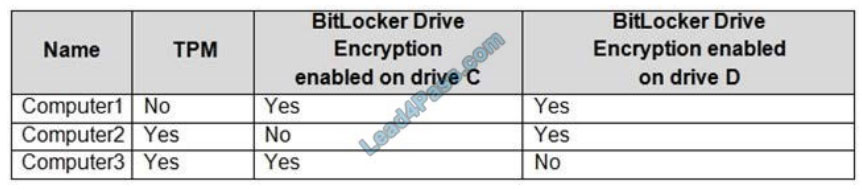
You have a removable USB drive named USBDrive1 that is encrypted by using BitLocker to Go.
You plan to use USBDrive1 on Computer1, Computer2, and Computer3.
You need to identify on which computers you can enable automatic unlocking of BitLocker on USBDrive1.
Which computers should you identify?
A. Computer2 and Computer3 only
B. Computer3 only
C. Computer1 and Computer3 only
D. Computer1, Computer2, and Computer3
The BitLocker key is stored in the registry when you enable auto-unlock but only if the operating system drive is encrypted with BitLocker. A TPM is not required.
QUESTION 9:
You have a workgroup computer that runs Windows 10.
You need to set the minimum password length to 12 characters.
What should you use?
A. Local Group Policy Editor
B. Credential Manager in Control Panel
C. Local Users and Groups in Computer Management
D. Sign-in options in the Settings app
QUESTION 10:
You have several computers that run Windows 10.
All users have Microsoft OneDrive for Business installed.
Users frequently save files to their desktops.
You need to ensure that all the users can recover the files on their desktop from OneDrive for Business.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Copy ADMX and ADML files to C:\Users\PublicDesktop\
B. From Backup in the Settings app, add a drive
C. Configure the Silently move Windows known folders to OneDrive settings
D. Copy ADMX and ADML files to C:\Windows\PolicyDefinitions
E. Configure the Save documents to OneDrive by default setting
References: https://docs.microsoft.com/en-us/onedrive/plan-onedrive-enterprise
https://docs.microsoft.com/en-us/onedrive/use-group-policy#KFMOptInNoWizard
QUESTION 11:
You have a computer named Computer1 that runs Windows10. Computer1 is in a workgroup. Computer1 contains the users shown in the following table.
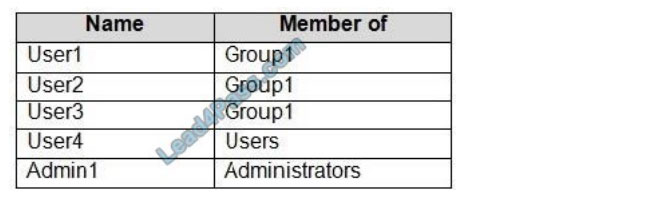
You need to apply the same Group Policy settings to only User1, User2, and User3. The solution must use a minimum number of local Group Policy objects (GPOs). How many local GPOs should you create?
A. 1
B. 2
C. 3
You can use security filtering to restrict the GPO to the required users. Only users with the Read and Apply Group Policy permissions will have the GPO applied to them.
QUESTION 12:
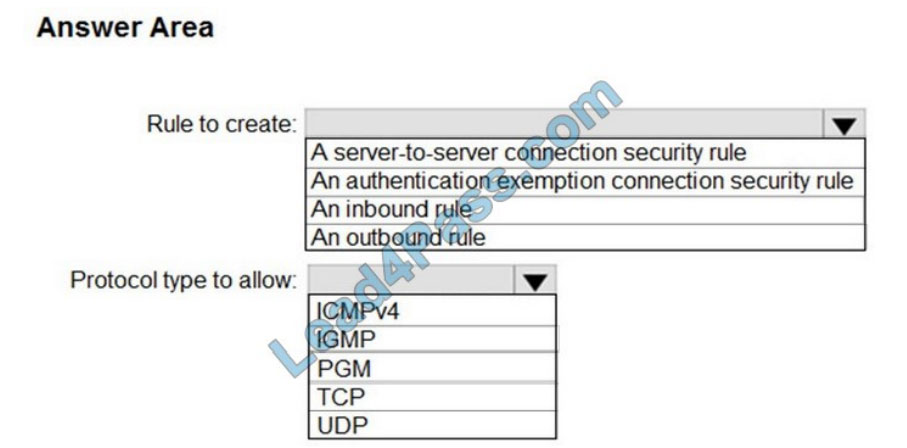
HOTSPOT
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10.
You need to ensure that Computer1 will respond to ping requests.
How should you configure Windows Defender Firewall on Computer1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
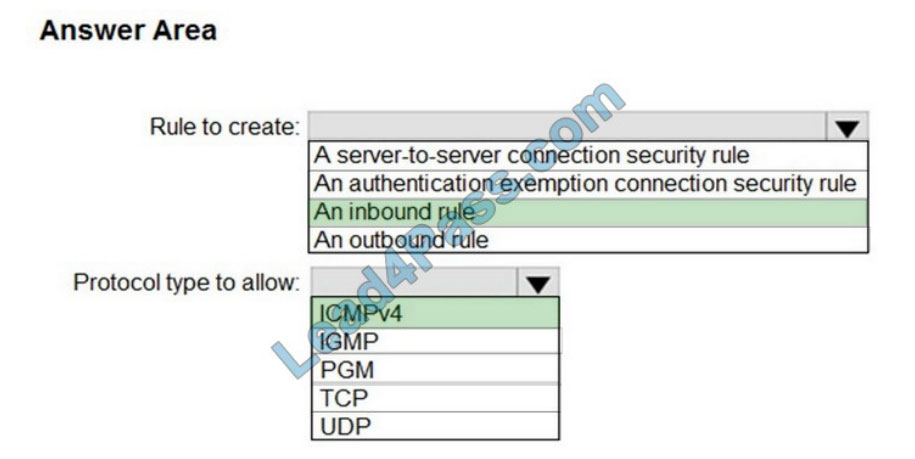
Correct Answer:
QUESTION 13:
HOTSPOT
You have a computer named Computer1 that runs Windows 10 and has the users shown in the following table.
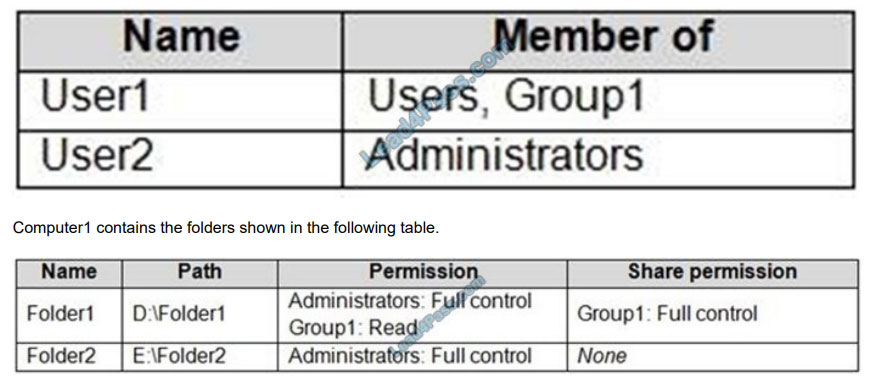
You move Folder1 into Folder2.
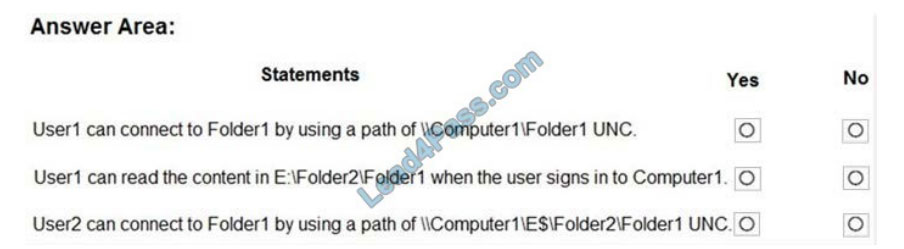
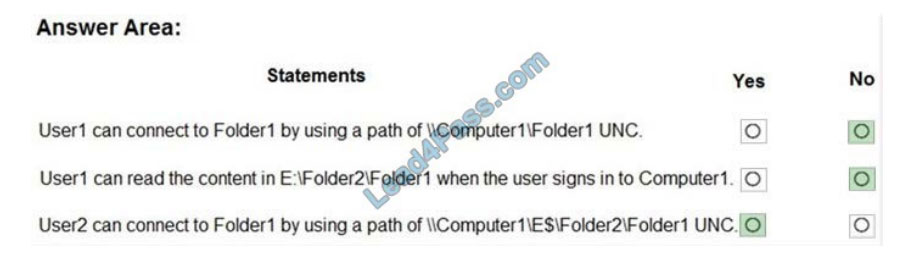
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
QUESTION 14:
HOTSPOT
You have a workgroup computer named Computer1 that runs Windows 10 and has the users shown in the following table.
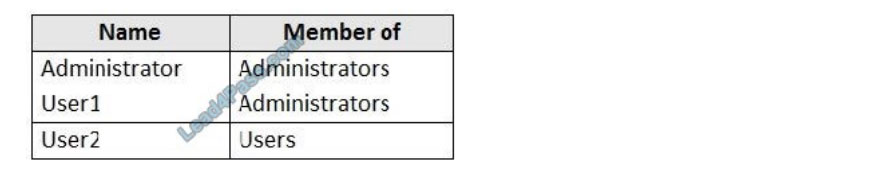
User Account Control (UAC) on Computer1 is configured as shown in the following exhibit.
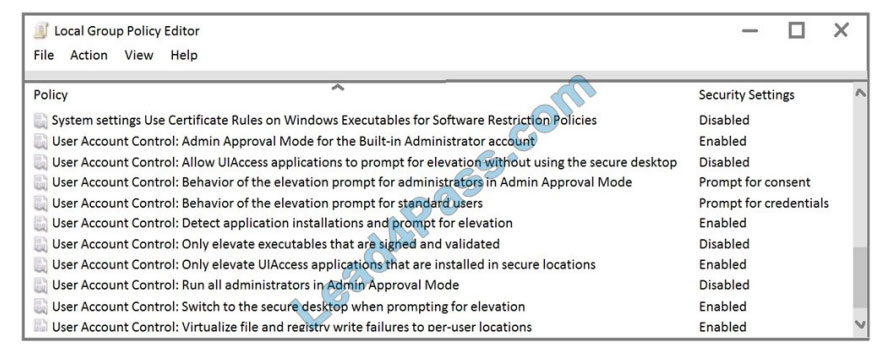
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
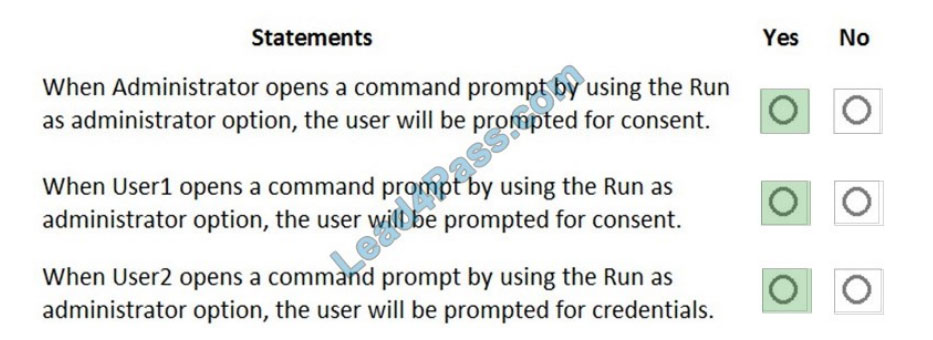
Box 1: Yes
User Account Control: The behavior of the elevation prompt for administrators in Admin Approval Mode is set to Prompt for consent When an operation requires elevation of privilege, the user is prompted to select either Permit or Deny. If the user selects Permit, the operation continues with the user\\’s highest available privilege.
Box 2: Yes
User1 is a member of the Administrators group.
User Account Control: The behavior of the elevation prompt for administrators in Admin Approval Mode is set to Prompt for consent When an operation requires elevation of privilege, the user is prompted to select either Permit or Deny. If the user selects Permit, the operation continues with the user\\’s highest available privilege.
Box 3: Yes
User Account Control: The behavior of the elevation prompt for standard users is set to Prompt for credentials (Default) When an operation requires elevation of privilege, the user is prompted to enter an administrative user name and password. If the user enters valid credentials, the operation continues with the applicable privilege.
QUESTION 15:
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10. Computer1 contains a folder named Folder1.
You plan to share Folder1. Everyone will have Read share permissions, and administrators will have Full control of share permission.
You need to prevent the share from appearing when users browse the network.
What should you do?
A. Enable access-based enumeration.
B. Deny the List NTFS permissions on Folder1.
C. Add Folder1 to a domain-based DFS namespace.
D. Name the share Folder1$.
Appending a dollar sign to a share name prevents a share from appearing when users browse the network.
Incorrect Answers:
Access-based enumeration will hide the share from anyone who doesn\\’t have permission to access the share.
However, as `Everyone\\’ has Read access to the share, the share would appear for everyone when they browse the network.
Publish the answer:
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| B | B | B | A | image | B | A | C | A | CD | A | image | image | image | D |
This is just a small test, and more questions are needed to pass the Microsoft MD-100 exam. For the complete Microsoft MD-100 exam dumps,
please visit https://www.leads4pass.com/md-100.html (Total Questions: 297 Q&A).
ps. More free Microsoft exam practice questions are available at fulldumps.com, which contains the complete Microsoft series: Role-based, Fundamentals, Specialty, Microsoft 365, MTA…
ps.
Share free Microsoft MD-100 exam PDF from a part of leads4pass MD-100 exam dumps:
https://drive.google.com/file/d/1cB-EJPZiqQB3Lxr4PXNVjkDyK6_4NSXU/